Category ArchiveExploits
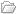 Filed under: Defacements, Exploits, Personal Opinions, Security News
Filed under: Defacements, Exploits, Personal Opinions, Security News
posted by D1m on 01 Feb 2007
MSN.co.uk Money Related Websites Hacked And Defaced
Two websites belonging to MSN (Microsoft Network) in the United Kingdom, were defaced today by an attacker who goes by the nickname “DARK LORD“. It looks like someone who is unethically testing his SQL injection skills, and “feeding” himself with a false sense of pride, just by leaving the message “DARK LORD WAZ HERE”.
No. I am not a defacer psychologist. I am just expressing my personal opinion on the matter, which is this: If a website defacement doesn’t convey a meaningful message, then it is done for selfish reasons.
A bit of an embarassment for Microsoft’s sysadmins…
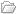 Filed under: Defacements, Exploits, Security News
Filed under: Defacements, Exploits, Security News
posted by D1m on 30 Jan 2007
Britney Spears’s Official German Website Got Hacked And Defaced
Was time for the website defacers to hit the music industry! Yesterday, visitors of the BritneySpears.de website could read “XTech Inc Onwed the Music Industry… and the rest of it ![]() ” at the top of the home page. It appears to me though, that they just did it for fun and not for any serious reason.
” at the top of the home page. It appears to me though, that they just did it for fun and not for any serious reason.
Apparently it was hosted in the same webserver with other official german websites of Sony BMG entertainment.
The attackers exploited a web application vulnerability – probably php inclusion – in order to get access to the Solaris 9/10 webserver.
 Filed under: Exploits, Security News
Filed under: Exploits, Security News
posted by D1m on 02 Dec 2006
Remote Root Exploit For Linux Kernel 2.6.x. At Auction!
It pays to get 0day remote root exploits for vulnerabilities! Digital Armaments Inc. – an IT security company based in the US – launched a hacking challenge on the 1st of November on the topic of “Remote Kernel Exploitation” . The challenge will end on the 31st of December and prizes will be given to the authors of the official advisory reporting the identified vulnerabilities which must result to remote code execution. The winning advisory will be then sold in an auction.
Although the official rules of the challenge forbid the disclosure of any vulnerability related information before the end of the challenge, according to the organizers, news information about important vulnerabilities that worth the early attention of the IT community should be made known before public disclosure of the related exploits. Continue Reading »



 OWASP
OWASP